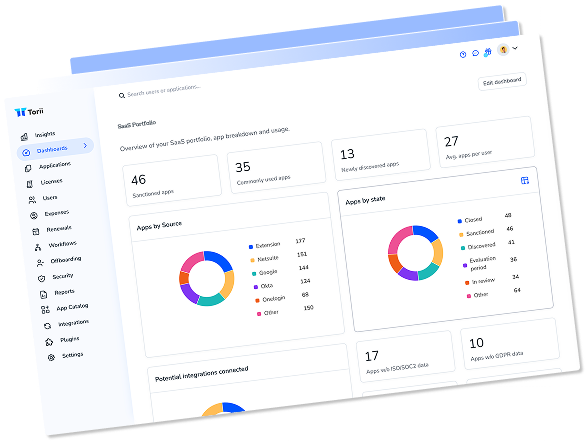
How to Detect Shadow IT in Your Organization

Shadow IT flourishes when new cloud tools pop up faster than policies can keep pace. Security teams feel it whenever an unsanctioned file-sharing site or AI bot drips data past approved guards. Plugging that leak starts with making hidden assets visible, then holding the owners of visible assets accountable. Procurement misses most of it, auditors miss plenty, but regulators and attackers rarely overlook a thing.
Real visibility demands a reliable list of approved apps, rich telemetry, and tight coordination with finance. Those layers add context, turning random log entries and invoices into clear indicators of risk. Combine that insight with plain-spoken outreach and the workforce will surface whatever remains in the shadows. Automation helps, yet it still needs a living inventory that teams review and update together.
Work through the five steps in order and you can tame shadow IT without smothering the ingenuity behind it.
Table of Contents
- Map Your Approved Tech Stack
- Mine Telemetry for Unknown Domains
- Deploy CASB and Discovery Tools
- Correlate Spend With Usage Data
- Create Continuous Feedback Loops
- Conclusion
- Audit your company's SaaS usage today
Map Your Approved Tech Stack
Start a shadow IT sweep by checking what you already pay for. Gartner puts the average midsize firm at more than 1,000 cloud apps, and a clear baseline keeps that figure from growing unseen.
Building that list means raiding data silos that rarely line up. A CMDB export might label an app one way, the SSO catalog another, and procurement records often stick with generic vendor names. Dump everything into a single sheet, then clean it up so “O365” and “Microsoft 365” merge into one record.
Save valuable time by using this short yet comprehensive collection checklist:
- CMDB or ITSM exports for servers, databases, and licensed software
- SSO provider catalogs for active logins and dormant connectors
- Purchasing and contract systems for legal vendor names and renewal dates
- Departmental share drives or wikis where teams track their own tooling
Documenting an app without understanding its data flows only tells half the story. Sketch which customer or employee data moves through each platform, who sends it, and where it lands; a quick Airtable or Visio diagram is fine. This mapping highlights hidden feeds, such as an HR system exporting to a marketing list, that could amplify risk if copied into an unsanctioned clone.
Tag every entry with an owner and the business capability it supports (sales enablement, payroll, customer analytics, and so on). When two tools sit in the same bucket, you have an early signal of duplication that may point to stealth purchases. Listing an owner also gives you a direct contact when later investigations need context.
Finally, post the inventory in a shared workspace, such as an internal wiki or SaaS management portal, then schedule quarterly check-ins. Automate new-entry forms so project managers can log fresh apps before they go live, keeping the list current rather than a dusty snapshot. A living, searchable catalog turns every future discovery into a quick diff instead of a week-long scavenger hunt.

Mine Telemetry for Unknown Domains
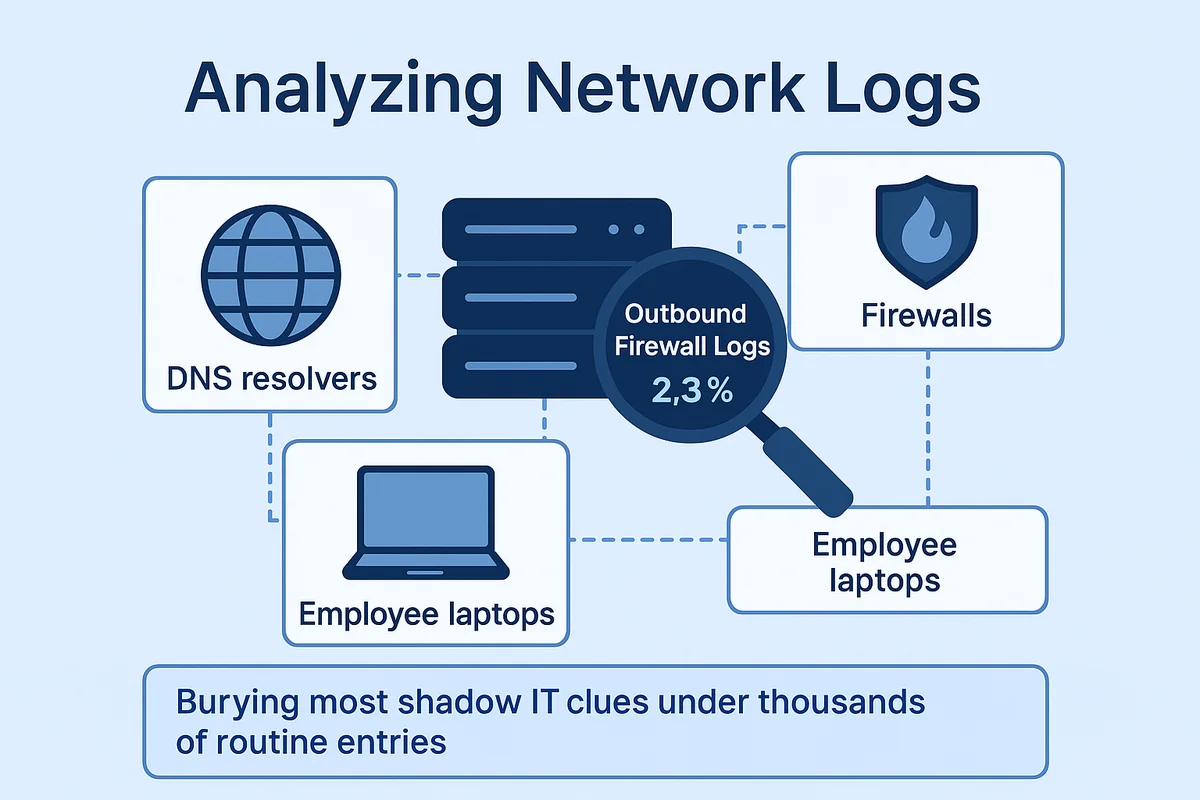
Network logs bury most shadow IT clues under thousands of routine entries. The real work starts by aiming collection at the right sources, firewalls, DNS resolvers, and employee laptops, then merging those feeds quickly before ring buffers overwrite yesterday’s evidence.
Outbound firewall logs pay off first because each packet advertises its destination. Export flows from Palo Alto or Fortinet hardware into Splunk, tag every record with the egress interface, and roll up requests by fully qualified domain name. After only a few hours, patterns emerge: marketing laptops ping design-tool APIs at 2 a.m., and finance desktops talk to cloud accounting sandboxes never blessed by IT.
DNS traffic often fills the gaps that web proxies miss outright. Cisco Umbrella, Windows DNS debug logs, and quick dig captures from roaming agents bring back hostnames that firewalls record only as shared IP addresses. After filtering out approved domains, the remaining chatter quickly shows which calls are just background telemetry and which point to a shadow SaaS tenant spinning up batch jobs at odd hours.
Flagged destinations need context before the SOC starts paging you. Run a quick WHOIS on each domain, then note the registrar, ASN, and hosting country in a spreadsheet for later sorting. Commercial risk feeds from Recorded Future or DomainTools make it easier to separate harmless code libraries from data-hungry apps.
- Sort domains by request count, bandwidth, and the number of unique devices
- Drop content delivery networks and known ad trackers to reduce noise
- Flag any domain tied to a personal email address for deeper review
- Pass the trimmed list to application owners so they can confirm actual use
Send the cleaned list back to the SIEM with a straightforward rule: alert when any new host touches a watch-listed domain. The policy stays quiet most days yet still catches the next unapproved file share before customer data lands in the wrong place. Re-baseline at least monthly so the inventory stays fresh and the team can watch shadow IT fade or mutate in near real time.
Deploy CASB and Discovery Tools
Manual audits miss plenty once cloud accounts multiply faster than the team can track. After you log the official stack, a CASB or SaaS discovery tool shifts monitoring from quarterly chores to a live radar screen. It pulls proxy logs or cloud APIs and checks every new domain, OAuth grant, and API key against a risk model that adjusts as soon as policy changes.
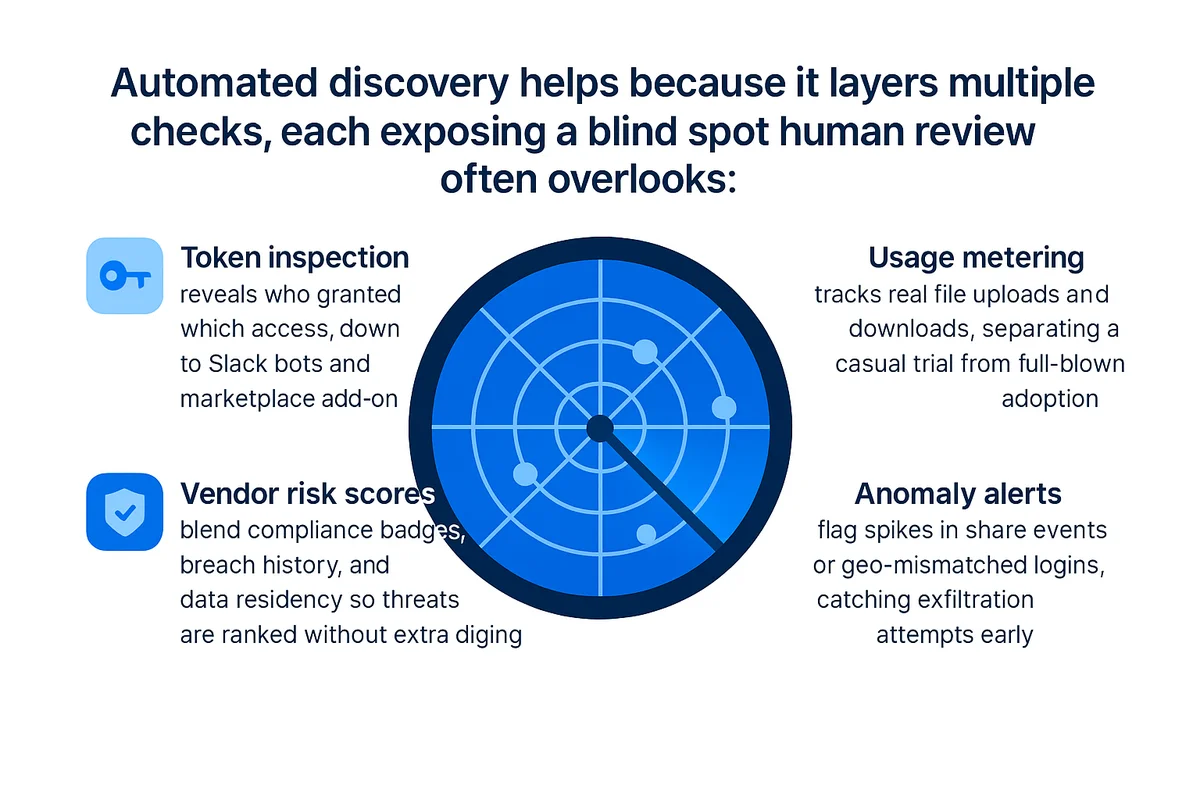
Automated discovery helps because it layers multiple checks, each exposing a blind spot human review often overlooks:
- Token inspection reveals who granted which access, down to Slack bots and marketplace add-ons.
- Usage metering tracks real file uploads and downloads, separating a casual trial from full-blown adoption.
- Vendor risk scores blend compliance badges, breach history, and data residency so threats are ranked without extra digging.
- Anomaly alerts flag spikes in share events or geo-mismatched logins, catching exfiltration attempts early.
Blocking a risky app should take clicks, not days of tickets. Connect the CASB to your identity provider so an unsanctioned account freezes right away and the owner hears about it. Teams that run Netskope with Okta have cut response times from days to minutes by linking discovery alerts to automated Okta Workflows, which freeze the user and open a service request. The same approach extends to SASE gateways like Zscaler or to Microsoft Defender for Cloud Apps if you already run on 365.
A clear dashboard closes the loop between discovery and executive action. Leadership wants a bar chart that contrasts sanctioned and discovered apps, adds cost estimates, and tracks trends. Gartner predicts 75 percent of corporate data will pass through unsanctioned cloud services by 2027; an hourly view keeps that risk in plain sight. Include a “top five new apps” tile so product managers can discover grassroots tools worth formal backing. Over time the chart should tilt toward sanctioned usage, proving the CASB is closing the gap between policy and reality.
Correlate Spend With Usage Data
Expense records cover blind spots that packet captures leave behind when you look for shadow IT. Because finance tracks every swipe, wire, and invoice already, their ledger can double as your radar screen. Gartner estimates that almost 30 percent of SaaS spend drifts unmanaged, so the CFO has a clear incentive to pitch in. Even recovering a fraction of that waste can bankroll security projects that have been stalled for years.
Pull the last twelve months of corporate card transactions alongside the vendor master file. Filter by merchant category codes that point to software or cloud services, then match each vendor against your approved-app list and SSO logs. Any charge with no obvious owner or login trail deserves a closer look or at least a brief spending freeze. Finance reconciles statements every day, so adding your inventory to their process requires little extra effort.
- Hunt for duplicate subscriptions masked by typos, such as “Dropbox Inc” versus “Dropbox*team.”
- Review small, recurring charges between $10 and $50; lightweight tools often slide past procurement.
- Match invoice seat counts against active users in your identity provider to expose shelfware.
- Tag renewals hitting within 30 days so you can shut them off before auto-pay fires.
Spend-analysis tools like Coupa or Ramp chart costs by cost center and by month. If the marketing card balance jumps right after a product launch, that surge may signal unsanctioned purchases, especially when fresh OAuth grants appear in your CASB. A heat-map view of those spikes shows managers where to swap in an approved option instead of sending one more warning.
Protect the savings by scheduling a quarterly review with finance, procurement, and security. Show up with a one-page scorecard outlining dollars recovered, contracts merged, and apps newly approved; hard numbers carry more weight than fresh policy slides. Before long the meeting feels routine, and that routine curbs shadow buying because everyone knows unsanctioned tools will pop up well ahead of their renewal date.

Create Continuous Feedback Loops
Shadow IT changes quickly, so your plan must keep pace. Quarterly cleanups leave long stretches of several months where unsanctioned apps can slip in, spread quietly, and take root. Ongoing feedback closes that gap by leaning on the people doing the work.
Start with a structured access-certification cycle anchored to the calendar. Every quarter, send each team lead a roster of the SaaS tools tied to their single sign-on group and ask them to confirm or remove. Cisco’s 2023 Security Outcomes Report found teams that certify access every 90 days suffer 37 percent fewer incidents than those that review yearly. Ask managers to note why they add any extras; their comments become a ready-made backlog for IT to review.
Make it painless for employees to flag new tools before a purchase happens. Lean on channels they already watch such as a Slack workflow or Confluence form. Approve low-risk trials within hours instead of weeks so people learn that sharing is the faster path.
- Add a one-question SaaS disclosure to new-hire orientation checklists
- Run an anonymous quarterly poll that asks, “Which tools help you work that IT may not know about?”
- Post a live dashboard of discovered versus approved apps on an internal site to spark friendly competition between departments
- Share a brief case study when a redundant license gets cancelled and budget flows back to the team
Sharing quick-win stories keeps the feedback loop lively and personal. When Figma surfaced unexpectedly in marketing, an anonymous survey spotted it within days, sparing design from re-entering data after a later shutdown. Highlighting that save in the company newsletter drove a 28 percent jump in voluntary disclosures the following month.
Feed those human insights into automated alerts from the CASB and finance logs. If a manager says a user no longer needs Asana, the identity platform should pull the license that night. Each cycle tightens the loop and shrinks the gray space where shadow IT hides.

Conclusion
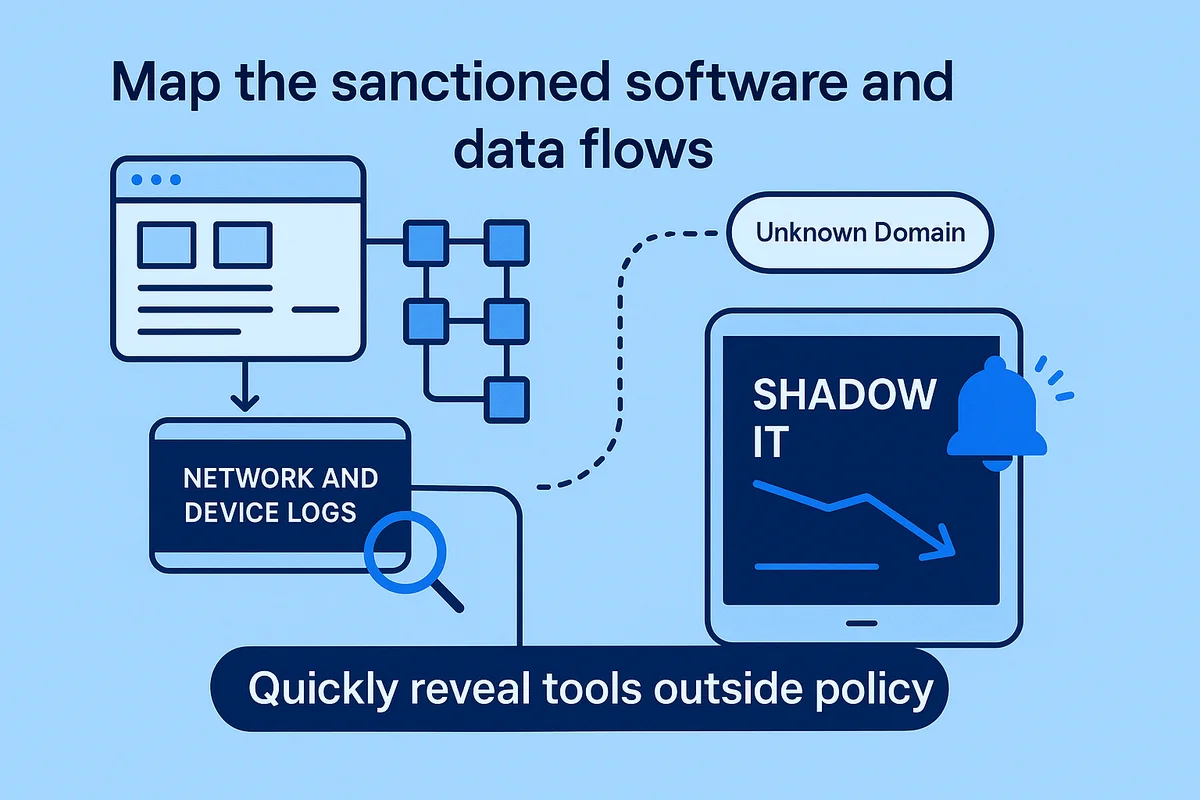
Shadow IT slips through the cracks at almost every growing company. Start by mapping the sanctioned software and data flows, then comb network and device logs for unknown domains; the contrast quickly reveals which tools run outside policy. A CASB with real-time alerts speeds up the search, sparing the team endless manual checks.
Combine spend records with usage data and loop in finance and end users. Follow these steps together and shadow IT turns into a visible, manageable slice of everyday security work.
Audit your company’s SaaS usage today
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the industry’s first all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
Learn more by visiting Torii.