What Is Employee Offboarding and Why Is It Important?
Employees move on, but their SaaS footprints can stick around for months. Each farewell often leaves active logins, OAuth tokens, and shared keys scattered across dozens of cloud tools, turning leftover access into both a security risk and a budget leak.
IT teams understand the risk, yet offboarding slips through the cracks because the work feels tedious and fragmented. Attackers need only one forgotten privilege to pivot, steal data, or wreck audit reports, and unused licenses keep burning cash until someone notices.
This article explains why automated, time-boxed offboarding across identity providers, SaaS sessions, license recovery, and audit trails matters to security, cost control, and compliance. We also share a step-by-step process to make the job far less painful.
Table of Contents
- What is SaaS Employee Offboarding?
- How does bad offboarding risk SaaS security?
- What is secure SaaS deprovisioning?
- How can offboarding cut SaaS license costs?
- Which compliance rules rely on offboarding?
- How do you automate offboarding for audits?
- Conclusion
- Audit your company's SaaS usage today
What is SaaS Employee Offboarding?
Employee offboarding in a SaaS-first company means turning off cloud access as reliably as you once collected a badge. Hardware handbacks still matter, yet the real attack surface now sits in hundreds of web apps quietly syncing data behind the scenes.
Effective SaaS offboarding works as a timed handoff between several internal systems. The employee status flips to “terminated” in the HRIS, the identity provider such as Okta receives that event, and every connected application must cut sessions immediately. This “last-day identity cutover” keeps data doors locked regardless of where the user worked, be it in an office, at home, or from an airport lounge. SSO makes the job easier, but only when every app joins the party. Direct logins to niche tools still lurk, and they demand extra care.
Hidden dependencies sprinkled throughout the stack quickly turn a clean handoff into a puzzle. A Zapier automation might post to Slack under the departed user’s token, while Jira tickets they owned feed sprint reports. Pulling the plug too late leaves data exposed; pulling it too early breaks live workflows. A precise sequence is critical: first transfer ownership, then revoke access to everything.
Plenty of teams assume that flipping a directory switch fully offboards an employee, but that switch is only the first step. OAuth refresh tokens stored on a phone, API keys embedded in a script, or offline IMAP sessions keep working until they are explicitly revoked. Personal devices add another wrinkle because wiping a SaaS token isn’t the same as wiping a laptop.
To close every gap, a secure and repeatable process should cover:
- Directory disable, SSO session kill, and API key rotation in one sweep
- Token revocation for every OAuth grant the user ever approved
- Ownership transfer of calendars, docs, and project boards before access ends
- Flagging apps that lack SCIM support for manual follow-up later
- Timestamped logs proving each step ran within the defined cutoff window
When these steps run on autopilot, offboarding stops being a frantic checklist and becomes a quiet, verifiable routine that scales right alongside your growing SaaS catalog.

How does bad offboarding risk SaaS security?
A single forgotten SaaS account can unravel months of security work overnight. Former employees know where source code lives and which dashboards hold customer details, so any door they can still open offers attackers a ready-made roadmap.
Security teams see the fallout up close every single year. In 2020 the Marriott breach traced back to credentials left active for two franchise workers months after they left, exposing data on 5.2 million guests. Okta’s latest “Businesses at Work” report found that 80 percent of investigated incidents started with an inactive account still present in an identity store. These aren’t edge cases; they’re the predictable result of sloppy deprovisioning.
Improper offboarding leaves loose threads that attackers tug at every day:
- OAuth tokens that never expire and skip MFA checks entirely
- API keys committed to GitHub by departing engineers, then cloned by threat actors
- Admin roles granted through IdP groups that no one audits after team reshuffles
- Personal devices with synced email or Drive files that remain outside MDM reach
DevOps and engineering teams, unintentionally, often compound the danger even more. Long-lived AWS access keys often sit in CI pipelines owned by a single user; if that person exits without a key rotation, the key survives in every build artifact. The 2021 Codecov attack started this way, allowing lateral movement into hundreds of customer repositories once a single bash uploader script was altered.
One unrevoked SaaS identity almost never stays isolated for long. Attackers pivot from a forgotten Jira account into Slack, pull environment variables, then jump into production databases that trust the same SSO groups. Each hop increases dwell time and the blast radius, turning what looked like a low-risk oversight into ransomware or insider-trading headlines.
Cleaning up after such an event costs far more than a disciplined offboarding checklist. Incident responders must hunt through weeks of logs, reset thousands of passwords, and reassure customers that controls work. Closing the gap before someone walks out the door is cheaper, faster, and kinder to the people who have to pick up the pieces later.

What is secure SaaS deprovisioning?
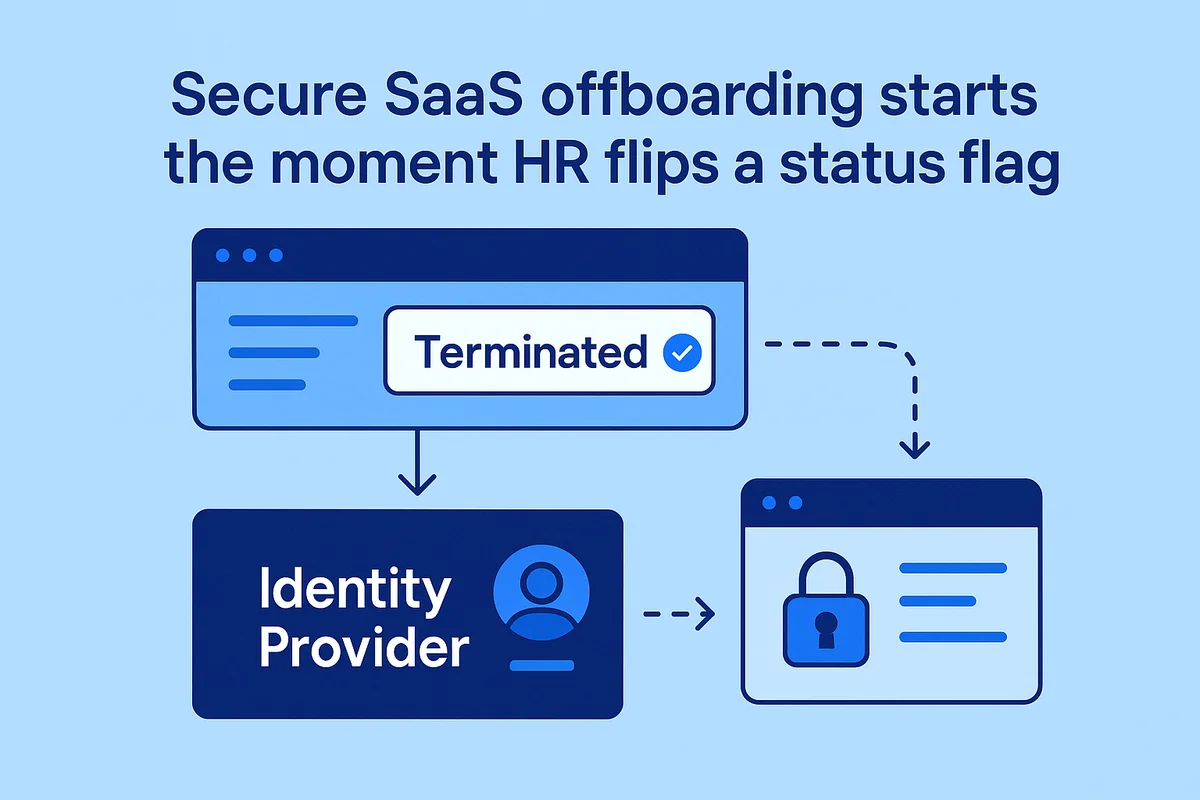
Secure SaaS offboarding starts the moment HR flips a status flag in the people system. That single update, often fired from Workday or BambooHR, must reach the identity provider within seconds so the departing employee’s sign-in sessions end before the last crumbs of their farewell cupcake. Miss that first hop and every downstream step drags.
The identity platform (think Okta or Azure AD) has to push the change to every connected app, not just freeze the core directory account. Session cookies, refresh tokens, and mobile push sessions stick around until they are revoked at the application layer; Salesforce reports show some tokens living six hours after an SSO block, more than enough time for a quick data grab. The runbook therefore ends live sessions first, shreds tokens second, and clears MFA factors last.
Teams that document the flow usually attach it to a repeatable checklist:
- HRIS marks “terminated,” triggering an SCIM or webhook event.
- IdP suspends the user, kills active sessions, and revokes OAuth refresh tokens.
- Critical SaaS apps run API calls to delete or transfer calendars, files, repos, channels, and virtual machines.
- Shared passwords and secrets stored in a vault rotate automatically, removing the user from groups that can view new values.
- Last, a service account posts a digest of completed steps to Slack for the audit trail.
Some resources left behind in the cloud require special handling. Long-running GitHub Actions, scheduled BigQuery jobs, and Terraform plans may still reference the ex-employee’s personal token. Flag those jobs during the sweep, attach a temporary bot credential, and record the ownership handoff so builds keep passing without exposing keys.
Keeping all of this on track takes automation, not heroics. SaaS management platforms like BetterCloud chain HR events to hundreds of APIs, while low-code engines catch one-off tools lacking SCIM. Even so, you still need a weekly scan for apps without integration hooks; a five-minute manual kill beats discovering an open door during your next penetration test.
How can offboarding cut SaaS license costs?
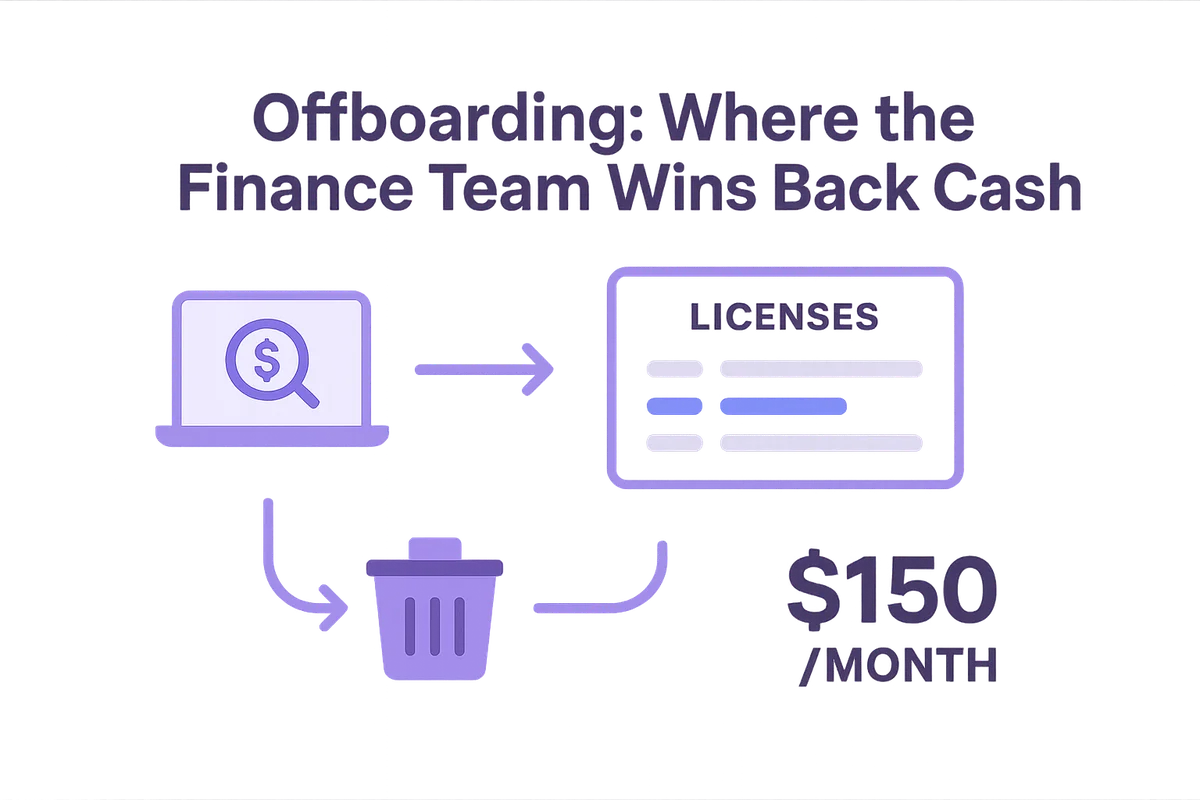
Offboarding is where the finance team wins back cash that crept out through idle SaaS seats.
When an employee leaves, every lingering license keeps billing like a taxi meter, even if nobody touches the app. Multiply that by premium tools such as Salesforce at 150 dollars a month and the leak becomes obvious.
With dozens or even hundreds of departed users on the roster, losses escalate fast.
Teams that claw back spend follow a simple playbook before the farewell cake is gone.
- Sync your license table with the HRIS every night so terminated users pop up automatically.
- Flag seats with no activity for 30 days, not just last login, to catch API-only usage.
- Reassign pricey licenses to waiting staff instead of buying new seats.
- Downgrade former admins to free viewer roles when you must keep historical data.
- Track shared mailboxes and test environments; they often carry hidden enterprise subscriptions.
Automation handles the tedious checks, but finance still owns the approval queue because accountability cannot be outsourced.
A quick calculator shows how the math rewards prompt action. A marketing org paying 65 dollars per Adobe Creative Cloud seat loses 650 dollars if a license idles for ten days; keep ten such seats idle for a quarter and the hit breaks ten thousand. Slice mean time to deprovision from 20 days to five and you reclaim 75 percent of that waste, with no productivity penalty. Put that saving against next year’s renewal and the CFO notices.
Right-sizing tiers delivers another silent win that many teams skip. Sales ops often forgets to downgrade legacy system administrators, leaving them on enterprise plans that cost triple a standard seat and often include audit modules they no longer need. Moving those dormant roles to read-only keeps data available for reference while aligning cost with real value.
Which compliance rules rely on offboarding?
Fast, airtight offboarding sits at the center of every security framework auditors track. Under SOC 2 control CC6.1 and ISO 27001 Annex A.9, a company must show user access shuts off the moment employment ends, not later that night and certainly not next quarter. HIPAA raises the bar by treating lingering credentials as a direct threat to protected health data. GDPR piles on with its data minimization rule: keep only what you need for only as long as you need it. Skipping any of these mandates can turn a routine HR update into a control failure.
These days auditors prefer evidence to theory; they ask for receipts. Expect a request like, “Provide logs for the last five terminated users proving access removal within 24 hours.” If your identity provider already feeds events into a SaaS management tool, those logs become a quick export instead of a week-long scramble. Solutions such as Drata gather the evidence automatically and flag any account that stayed live. That immediacy frees the security team to tighten process rather than chase screenshots.
Regulated data brings extra cleanup steps many teams often overlook:
- Encrypt any exported mailboxes or cloud drives before archiving.
- Purge personal health or financial info from SaaS backups once retention deadlines pass.
- Migrate shared Slack channels the user owned so audit trails remain intact.
- Capture a chain-of-custody record when files move between systems or owners.
Skipping any of these steps leaves sensitive data strewn across systems, creating an audit finding in waiting.
Even with good intentions, compliance still goes beyond simply passing audits. Smaller fines land daily from state privacy laws that mirror GDPR, yet even a ten-thousand-dollar hit hurts more than an automated workflow subscription. Legal officers also remind boards that delays can trigger breach notification rules, inviting lawsuits and brand damage long after the employee hands in a badge.
Measure offboarding speed, log every touchpoint, and prove it continuously. Do that, and the next evidence request becomes routine instead of panic.

How do you automate offboarding for audits?
Staying ready for an audit means tracking offboarding metrics as they happen. Security can make assumptions, yet auditors still want numbers and timestamps. When signals appear right away, missed steps get caught before they can mature into formal exceptions.
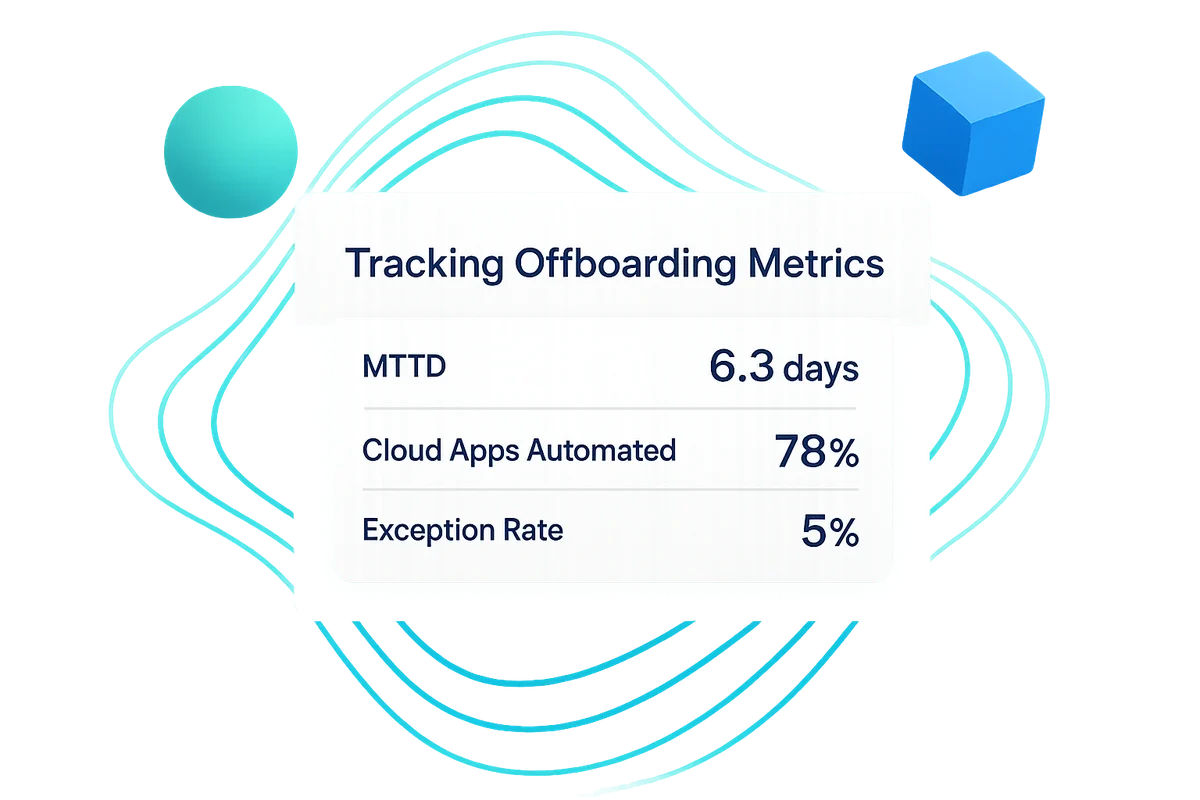
Start by locking in three core indicators that translate cleanly for both CISOs and finance, then track them relentlessly:
- Mean time to deprovision (MTTD) from HR termination date to final SaaS logout
- Percentage of cloud apps covered by automated offboarding versus manual playbooks
- Deprovisioning exception rate, the share of terminations with at least one failed step
When captured every day, these figures replace gut feel with hard evidence. Over a quarter, the trend shows if the program is tightening or drifting, and that clarity often opens the door to more automation.
Collecting these details is simpler when every event flows through one hub. A typical setup connects the HRIS to the identity provider, then routes user changes into an orchestration layer like Okta Workflows. Each action, whether disabling an account, revoking a token, or transferring a folder, triggers a webhook that drops a JSON log into the security information and event management system. With the fields mapped correctly, the SIEM serves as the evidence vault auditors want.
Metrics lose most of their value when drift goes unnoticed. Run quarterly tabletop tests that replay a high-risk departure and observe each automation as it fires. Any missed log write should spark a Slack alert and open a ticket on the spot, closing the loop quickly.
Make the offboarding goal visible and shared across every team. Publish a service level objective most people can recite in an elevator: all SaaS access gone within fifteen minutes of termination. Feed the three KPIs into a simple dashboard alongside the SLO so legal, HR, and engineering all see the same numbers. If one metric slips, the chart turns red and the owner gets a prompt. By the time the auditor arrives, a month’s worth of timestamped proof is ready for export.
Conclusion
When employees walk out, the apps they used keep running in the background. Modern offboarding steps in immediately, killing OAuth tokens, rotating keys, severing SaaS access, and passing files to the next owner before drift creeps in. That same flow also cuts unused licenses, curbs hidden spend, and captures solid audit evidence.
Track those metrics and automate every handoff, and your departures stay routine instead of risky. Run it the same way every time, and offboarding turns into a built-in guardrail that shields data, saves money, and satisfies auditors the moment they ask.

Audit your company’s SaaS usage today
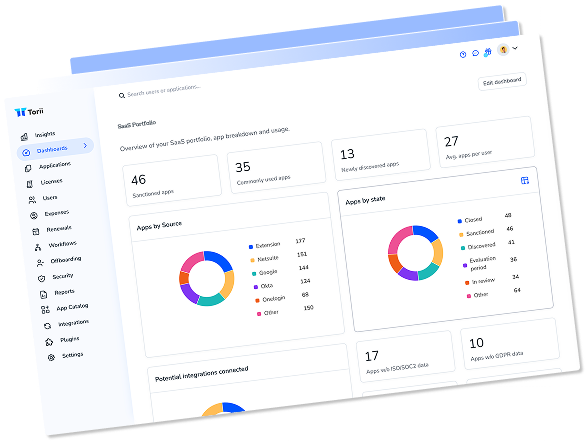
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the industry’s first all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
Learn more by visiting Torii.