10 Questions Government Agencies Must Ask SaaS Vendors During a Security Review
Buying cloud software in the public sector feels as perilous as it is essential. Each purchase order now brings questions about FedRAMP scope, encryption strength, and whether last year’s breach headlines could repeat on your watch.
Security teams no longer grant blanket trust, yet procurement timelines keep shrinking. When agencies front-load the right technical questions, they expose gaps early while sales representatives are still paying attention. Data residency, identity controls, and incident response may look routine; each can still derail a contract unless you ask for concrete evidence and timelines. Ten tightly scoped questions change that exercise into a playbook analysts can reuse.
Use them to satisfy compliance mandates, flag weak vendors early, and keep mission data where it belongs.
Table of Contents
- How do you keep data within approved regions?
- Which FedRAMP or StateRAMP authorization do you have?
- What encryption protects data in transit and at rest?
- How is identity and access managed securely?
- What logging and monitoring data will you share?
- How do you manage vulnerabilities and pen testing?
- What is your incident response process?
- Which sub-processors are in your supply chain?
How do you keep data within approved regions?
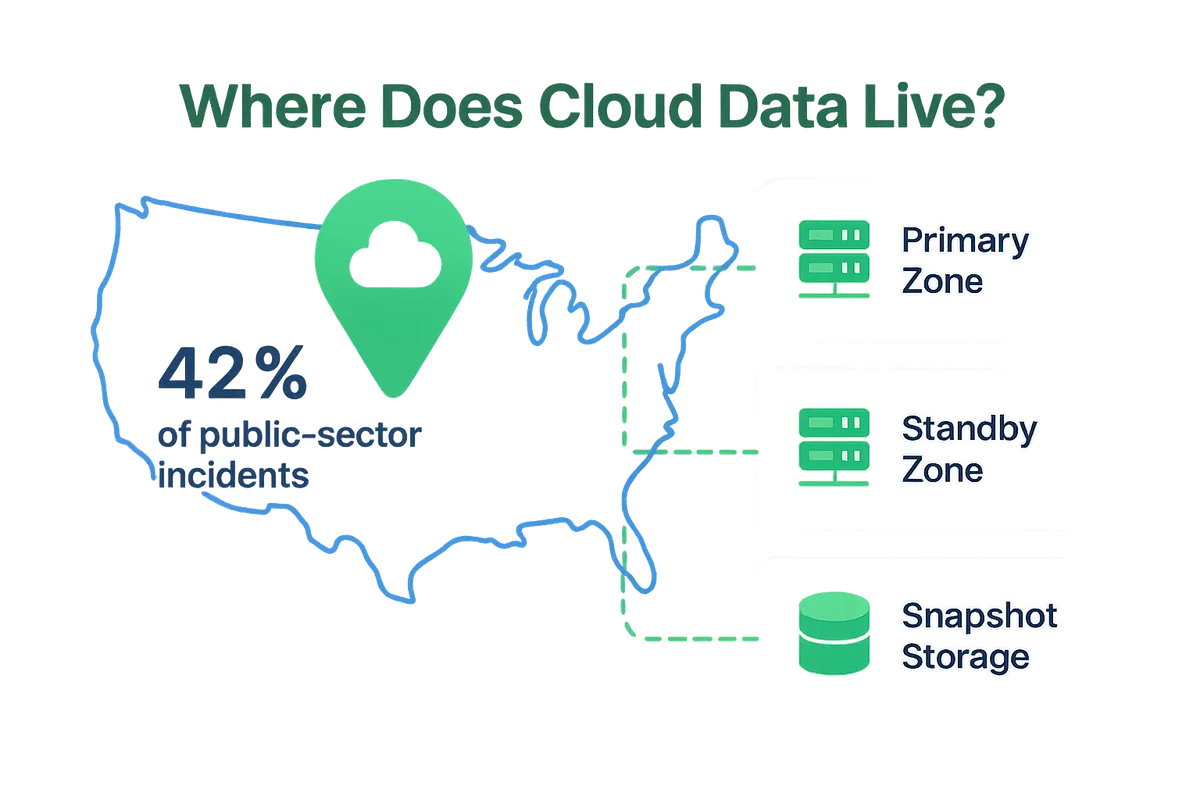
Pinpointing where cloud data lives sounds easy, yet one overlooked detail can stall an Authority to Operate for months. Agencies expect the vendor to list every region, availability zone, and backup target that could ever store production or disaster-recovery data. A simple “U.S. Only” pledge falls short when CJIS or IRS-1075 auditors want street addresses and lease agreements.
Request a diagram that pins the primary zone, standby zone, and snapshot storage. Line it up with your boundary map and flag any gaps. If you support multiple programs, insist on separate tenants so a state-tax dataset never co-mingles with a public-health workload. Gartner reported that 42 percent of public-sector incidents trace back to unintended data migration, so treat isolation as a hard control, not a theory.
Start by confirming the vendor supplies these technical and contractual guardrails:
- Region-locking controls that refuse API calls outside a whitelisted zone.
- Customer-managed replication policies that keep backups inside the same sovereignty ring.
- A “consent required” clause before the vendor can add new sub-processors or move workloads.
- Dedicated sovereign regions like AWS GovCloud, Microsoft Azure Government, or Google Cloud US regions where federal export rules already cap personnel access.
Even with these measures, verify that no silent partner sits in an unapproved jurisdiction. Request the living sub-processor list and match it against state data-localization statutes; six weeks’ notice is common, but not guaranteed, before a new party joins the chain. Watch for vague lines such as “global cloud footprint” in marketing decks, because if the vendor cannot map the bits today, they will struggle to document shifts tomorrow.
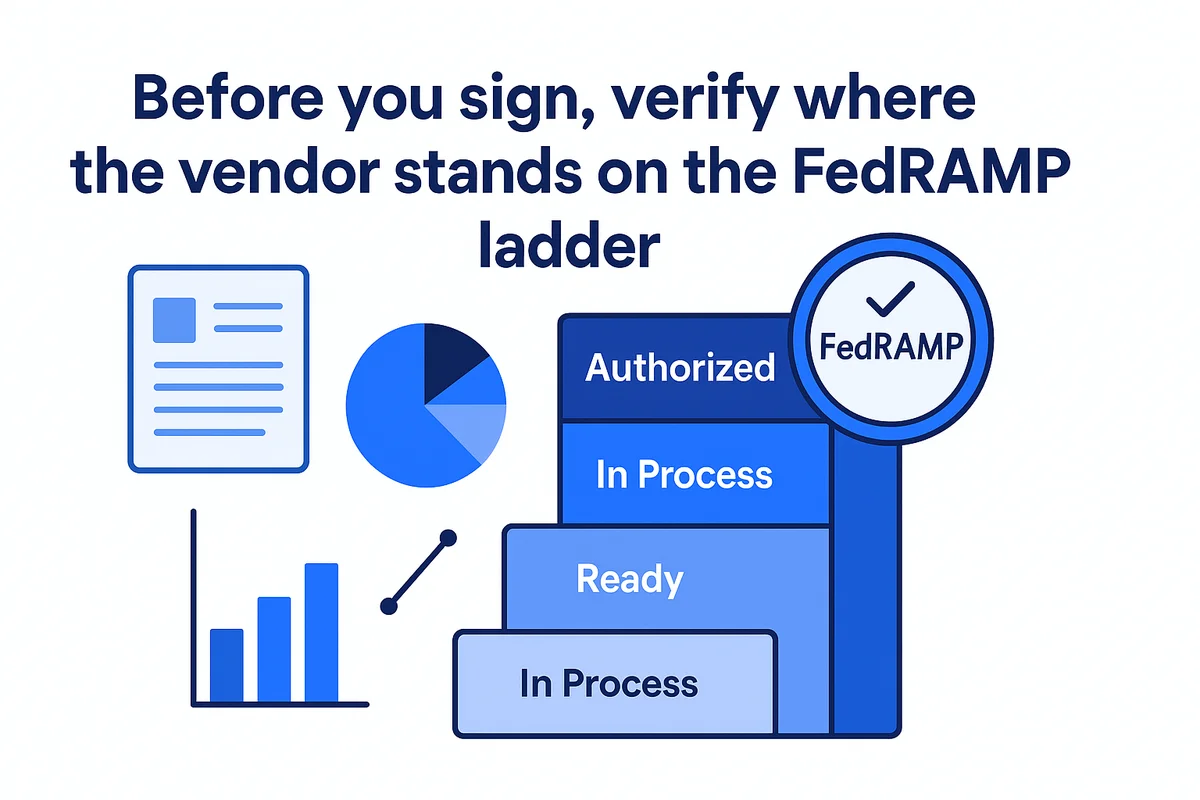
Which FedRAMP or StateRAMP authorization do you have?
Before you sign, verify where the vendor stands on the FedRAMP ladder. “Ready” means documents are drafted but no agency sponsor has stepped up, making your program office the guinea pig. “In Process” shows a sponsor is already guiding the package through the Joint Authorization Board, often trimming three to six months from your Authority to Operate timeline. An “Authorized” vendor, such as Amazon Web Services GovCloud, delivers an approved boundary you can inherit right away.
A FedRAMP ATO still needs solid evidence behind the seal. Request the System Security Plan, the current Plan of Action and Milestones, and the most recent 3PAO penetration report; together they surface open findings, compensating controls, and any scope creep. State agencies can confirm whether those same artifacts satisfied StateRAMP or aligned with TX-RAMP, since both trace back to NIST 800-53 but follow distinct reporting calendars.
Send the vendor a tight hit list so reviews don’t stall for weeks, and you both stay on schedule.
- Provide the FedRAMP ID number and date of current authorization.
- Share all change requests submitted since the last maintenance window.
- Flag any tooling gaps that block inheritance of controls SC-7, AC-17, or SI-4.
- Disclose DoD Impact Level reciprocity, if claimed, and the exact IL boundary.
- Commit to quarterly updates of the POA&M, even when no findings change status.
Align your overlay controls before the kickoff call to avoid late surprises. Map your agency’s high-value asset requirements to the cloud boundary, noting where you must add SC-28 media protection or IR-5 incident monitoring. Use the vendor’s ATO timeline to anchor contract milestones; if the renewal date lands inside your fiscal year, build that reassessment workload into the budget now instead of scrambling for funds later.
What encryption protects data in transit and at rest?
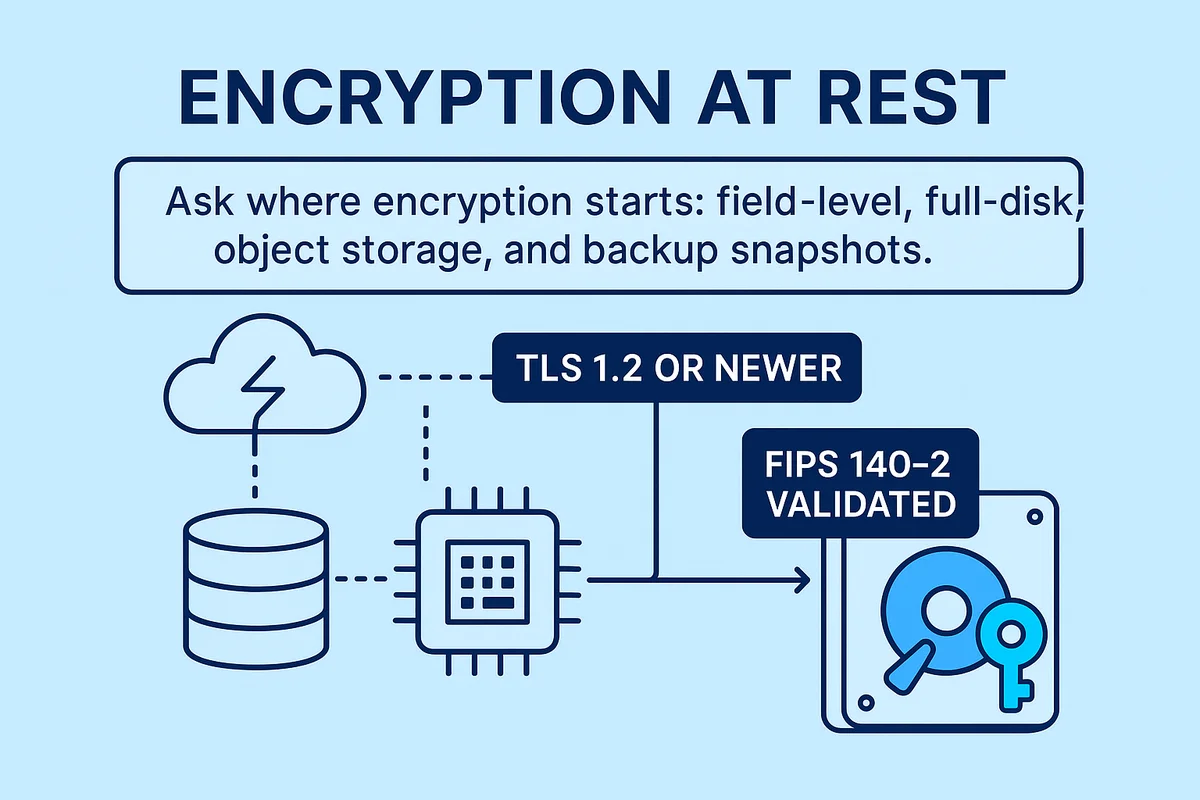
Agency records bounce between cables, databases, and processors before they finally land in storage. At each hop the encryption rules decide who can peek and who stays blind. Ask the vendor whether every connection is forced to TLS 1.2 or newer and whether downgrade attacks are blocked by HSTS plus perfect forward secrecy. For stored data demand FIPS 140-2 validated modules, not merely “compliant” code; that one word separates proven hardware from empty marketing.
Encryption at rest helps only when coverage is complete, not just on the convenient tables. Push for specifics on where encryption starts: field-level, full-disk, object storage, and backup snapshots. Ask whether server-side controls are backed up by client-side protection for extra-sensitive fields. If the vendor relies on native cloud storage, have them present the exact KMS setup and an audit trail proving customer keys never leave a FIPS boundary.
Keys guard the castle, so the rules around them matter even more than the cipher. Confirm you can bring your own keys through a dedicated KMS or a hardware security module you manage. Set expectations for automatic rotation every 365 days or less, and find out which team holds break-glass access so you can keep duties truly separate. If keys replicate across regions, insist the copies stay inside the legal boundary you already approved.
Threat models change, so your checklist has to stretch beyond today’s AES and RSA playbook.
- Is AES-256 applied by default across all workloads, or does it kick in only after a special request?
- What proof can you share that cryptographic libraries were compiled from source, signed, and never sideloaded from unknown repos?
- Can the platform isolate memory so data stays encrypted throughout processing, perhaps by using hardware-based confidential compute environments?
- Does the service integrate seamlessly with customer-owned HSMs such as AWS Key Management Service or comparable on-prem devices you already trust?
- How often does the team review supported cipher suites against fresh NIST SP 800-175B guidance and other cryptanalysis findings?
Before signing anything, request an executive summary of the last crypto agility exercise; the report shows how fast the vendor can swap algorithms when quantum-resistant standards appear.
How is identity and access managed securely?
Identity gates access to every cloud tool your agency hopes to use. Ensure that the provider already federates through SAML 2.0 or OIDC, letting you park all credentials in Azure AD, Okta, or whichever IdP you run. If the platform can’t carry PIV or CAC certificates from login to logout, brace for weeks of custom code and waiver paperwork you don’t want.
After identity, turn the spotlight to the real strength of your multifactor setup. Check that the product ships with FIPS-validated HOTP or TOTP tokens, and that a near-term plan exists for FIDO2 or WebAuthn keys that sidestep phishing kits. Verizon’s 2023 Data Breach Investigations Report says 74 percent of breaches still begin with stolen credentials, which means password-plus-SMS will fail any serious review. Get proof that admin logins require MFA on every authentication, not just the first time a device joins.
The set of roles and permissions deserves the same hard look as authentication itself. Ask the provider to include a starter policy where the top role can’t also access billing or support tickets. Confirm that every API endpoint checks the same entitlements. Look for support for:
- Attribute-based access that factors user clearance or project codes
- Time-bound or just-in-time elevation with automatic rollback
- Delegated administration scoped to a single tenant or agency bureau
- Session recording and real-time alerting on privileged commands
Strong lifecycle hygiene keeps those clean entitlements from decaying the week after launch. SCIM 2.0 or a similar API should create, change, and disable users within minutes of an HR event, wiping out orphan accounts. Some providers, like Duo Security, publish connectors that light up in an afternoon; others hand you CSV templates that fail without warning. Make them retire a contractor during the demo and then prove that the revoked token can no longer touch the API.
Tie every control back to NIST 800-63 rev. 3 assurance levels. Level 2 often covers public data, but anything touching PII or tax records jumps to AAL3 and needs hardware-backed keys. The right provider hands you a matrix showing which users sit at which level, how they watch for drift, and who signs off on exceptions. Skip that matrix and you’re buying promises, not protection.

What logging and monitoring data will you share?
Logs truly matter only when your team sees them almost immediately. During a SaaS review, skip the slideware and pin down how, where, and when raw events hit your SIEM. Get the schema in advance; mismatched fields or off-by-one timestamps quietly break the correlation rules you already trust.
When the conversation turns to commitments, pin the vendor to details:
- Streaming of authentication, admin, and API events within 60 seconds via HTTPS or TCP syslog.
- Minimum 365-day hot storage plus seven-year cold retention that matches your agency policy.
- Field-level audit trails that record before and after values for every configuration change.
- Log integrity sealed with SHA-256 hashes and daily Merkle-tree proofs.
- Delivery options that include direct write to Splunk, Elastic, or an S3 bucket you own.
Federal teams also need proof the vendor watches its own dashboards. NIST 800-137 calls for automated triggers, yet a 2022 CISA review showed 40 percent of cloud incidents were spotted by customers first. Ask for the SC-38 Continuous Monitoring report and note any high-severity alert that lingered longer than a week. If the provider leans on a managed detection firm such as Expel, press for service tier and acknowledgement time, not just the “24×7 monitoring” slogan.
Secure your own copy of the data before an outage or contract spat ever happens. The safest design writes a second copy to an immutable bucket in your tenant, away from the vendor’s production gear. That separation keeps evidence within reach for forensics or FOIA even if the service stops.

How do you manage vulnerabilities and pen testing?
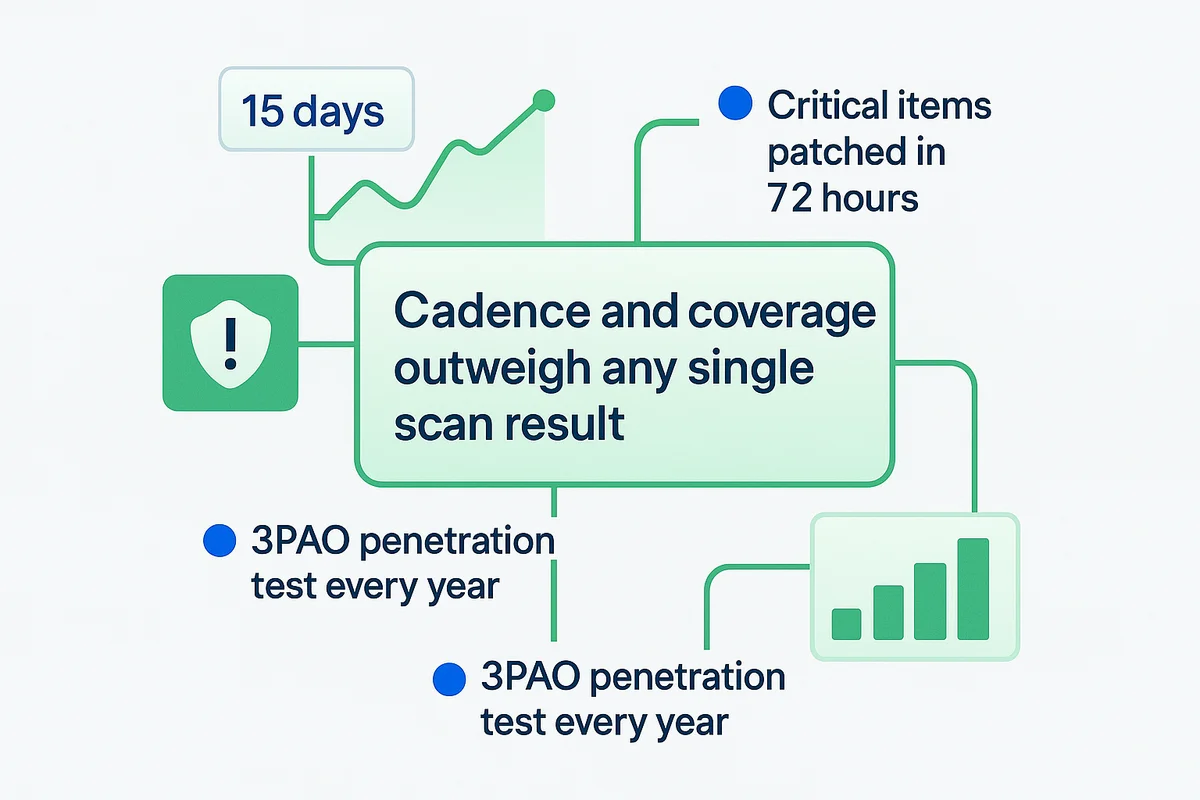
Vulnerabilities age like milk, so cadence and coverage outweigh any single scan result. Plenty of providers boast “continuous scanning,” yet the real test is whether those scans are credentialed, run on production replicas, and include container images that spin up and down within minutes. Without that depth, even the busiest dashboards can miss the flaw that ruins a weekend.
When you evaluate a vendor, press for numbers, not adjectives. Ask if the team aligns remediation windows with CVSS scores and the CISA Known Exploited Vulnerabilities list, committing to patch critical items inside 72 hours and highs within 15 days.
Automated scanning only reveals so much, so bring up people-driven testing. A FedRAMP-authorized 3PAO penetration test every year is the floor, not the ceiling. Quarterly dynamic application security testing, semiannual red-team exercises, and surprise social-engineering drills expose chained exploits that static tools miss, such as privilege escalation after a phishing entry point.
The strength of a vendor’s response also hinges on the development pipeline. Ask whether the vendor blocks merges on failed security checks, tracks dependency drift with a software bill of materials, and signs artifacts to stop tampering between environments. If they cannot produce an SBOM in SPDX or CycloneDX today, plan on carrying that risk yourself.
Artifacts worth seeing before you sign
- Current vulnerability management policy with CVSS-based service-level objectives
- Last three internal scan summaries with false-positive rates and trending data
- Most recent 3PAO penetration-test report, including evidence of remediation
- Red-team or purple-team scope, methods, and after-action findings
- Sample SBOM for a microservice, showing dependency mapping and license data
- Evidence of onboarding to CISA KEV feeds and automated ticket creation in the vendor’s backlog
What is your incident response process?
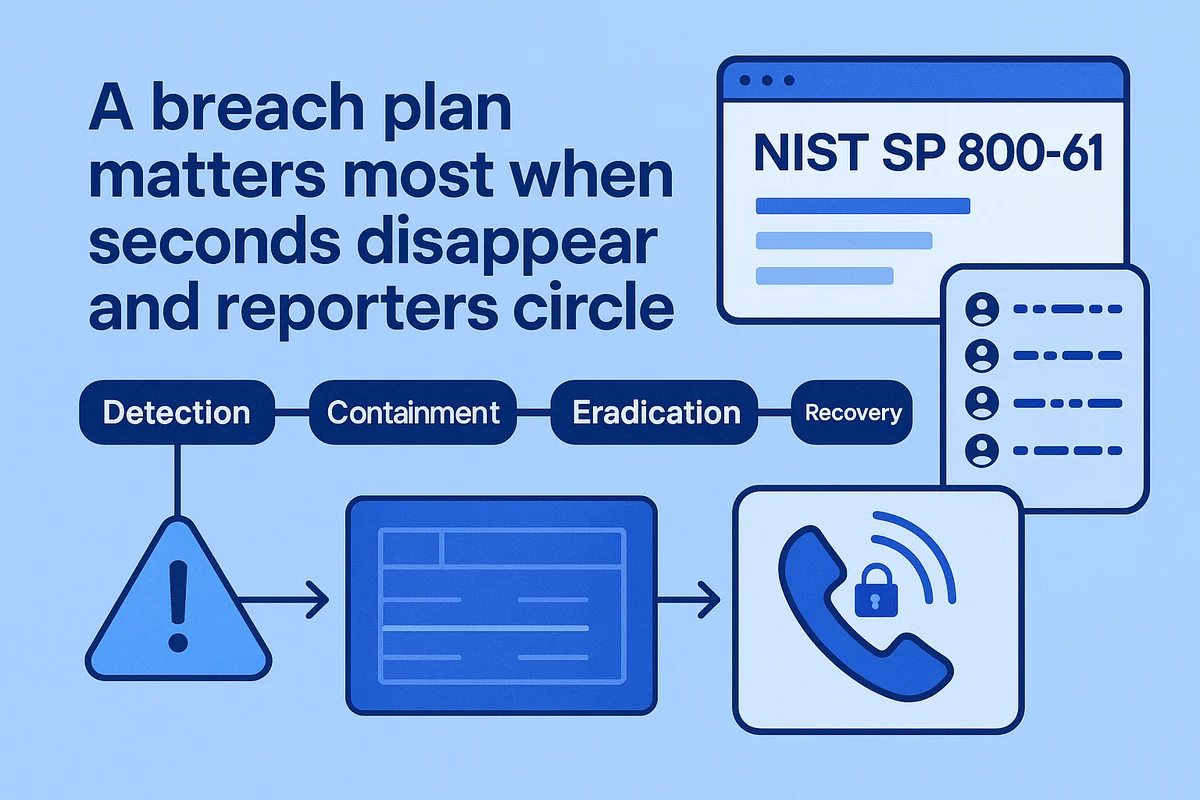
A breach plan matters most when seconds disappear and reporters circle. Ask the vendor for a living incident response playbook mapped to NIST 800-61 that explains detection, containment, eradication, and recovery in plain language. One critical detail: confirm the clock starts at first indicator, not after full confirmation, so the one-hour federal notification rule remains achievable. Request the exact escalation ladder, listing names, roles, and on-call numbers to prevent a scramble when time is slipping away.
Clear communication channels stop panic from turning into full-blown chaos. Insist on an encrypted hotline plus a fallback route in case primary networks go down. Signal or a private Mattermost space keeps attachments end-to-end protected and audit-ready. Ask how you will join the response. Will you get view-only access to the ticket queue, or a seat in their virtual war room with authority to approve containment steps? Early involvement speeds decisions and limits collateral damage.
Plans age quickly without pressure testing, so make tabletop drills mandatory. Ask the vendor to schedule at least two joint exercises per year, one announced and one unannounced, and to document both successes and missteps. Probe for supporting evidence:
- Date and scope of the last full-scale simulation
- Red-team or purple-team injects used to mimic insider threats
- Mean time to detect and mean time to contain metrics from the drill
- Changes shipped to production as a direct result of lessons learned
Still, paper proofs carry less weight than lessons from real incidents. Request a sanitized after-action report from the last breach, including root cause, data affected, and customer outreach timeline. Match those facts to the promised SLAs; gaps hint at future pain. Finally, lock all of this into the contract with financial penalties tied to missed notifications or ignored playbook steps. Accountability turns a glossy incident response deck into a safety net your team can trust.
Which sub-processors are in your supply chain?
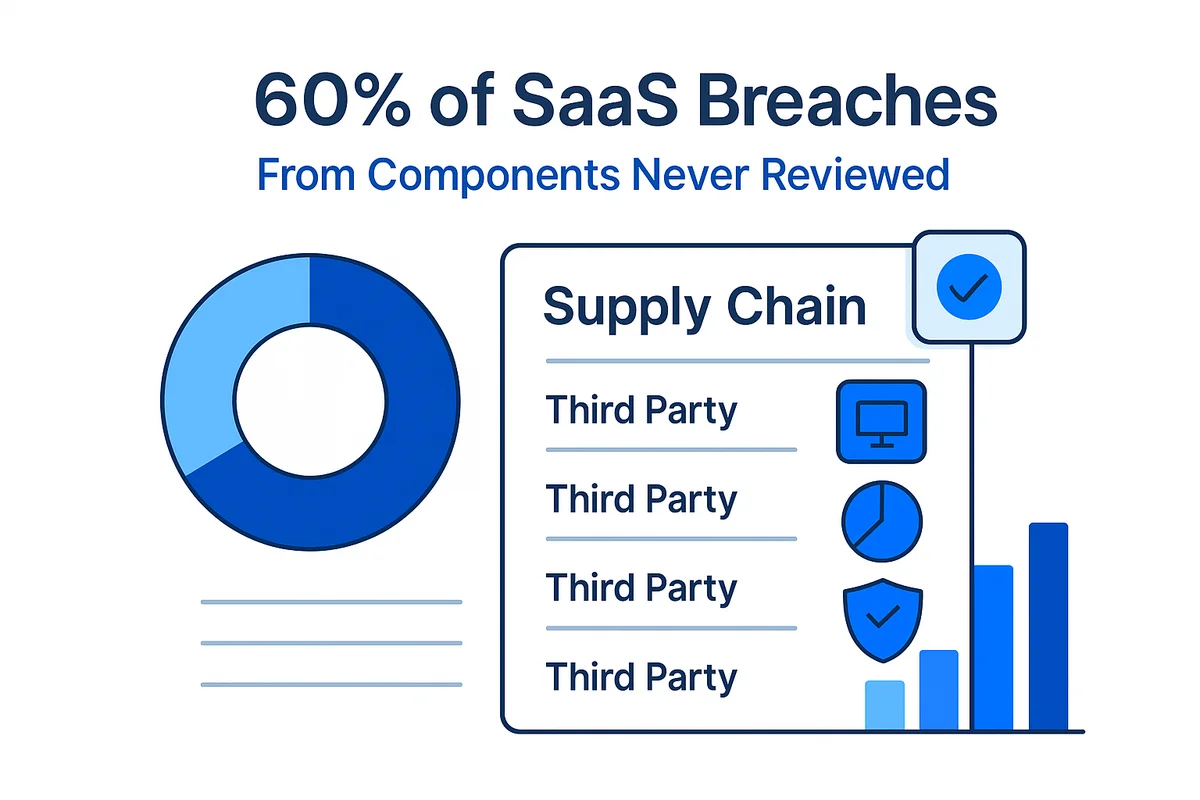
Mapping your SaaS provider’s supply chain comes first when you decide whether to grant an authority to operate. Third-party hosts, plugins, and contractors may sit outside FedRAMP boundaries; they still handle log streams, backups, or support tickets packed with regulated data. Gartner now attributes 60 percent of SaaS breaches to components customers never reviewed, so keep a current record of every name, scope, and compliance badge.
Ask the vendor for an up-to-date sub-processor list that covers every organization with logical or physical access to your environment. It should show service type, data elements handled, hosting regions, and the latest audit results. When a provider builds on hyperscale IaaS, confirm that its account pins your agency’s workloads to the regions cleared in your own overlay. A monthly export works for slow-changing setups, yet modern SaaS stacks swap partners all the time, so real-time change alerts matter.
During negotiations, push for the following details to appear explicitly in writing:
- Legal name, street address, and direct point of contact
- Function performed, such as content delivery, SMS, or customer support
- Applicable certifications or attestations, for example SOC 2 or FedRAMP Moderate
- Date of onboarding and last risk review
- Planned data flow diagram that shows ingress, storage, and egress paths
Downstream risk still lingers long after you receive the list. Flow-down clauses need to hold each sub-processor to your incident windows, encryption settings, and patch deadlines. If a CDN partner loses FedRAMP reciprocity, the SaaS vendor should reroute traffic or pause the link until the gap closes. Some agencies reserve the right to run joint audits once cascading risk hits a set threshold, avoiding surprises in the middle of a contract.
Timing makes the difference between action and regret when data might leave the country. Set 30 days’ notice for routine additions and same-day notice for any change that shifts geography or control inheritance. Vendors like Cloudflare post real-time dashboards that capture these moves, while Okta pipes alerts into its System Log. Feed that stream into your SIEM to detect new sub-processors automatically and kick off due diligence before production traffic flows.
How do you handle data retention and destruction?
Plans for exiting a platform matter just as much as onboarding in regulated environments. When an agency skips exit planning, orphaned records and stranded keys can turn a routine off-ramp into a year-long audit headache.
Start by pressing your vendor for retention controls you can configure, not just default schedules buried in the UI. Many agencies need 5-, 7-, or even 75-year holds, and the schedule often changes after litigation or a FOIA request lands. Ask them to map each data class, including user content, metadata, and system logs, to its own timer.
- Confirm whether any retention clock can pause automatically during active litigation holds.
- Check whether deleted objects remain in soft-delete or versioned buckets.
- Determine the retention period for encrypted backups after the primary wipe.
Once retention is sorted, shift your focus to practical data portability. A clean export beats an expensive e-discovery pull every time. Require the provider to support open, machine-readable formats such as CSV, JSON, or Parquet, and to document schema versions so you can validate completeness. For large volumes, a physical appliance like AWS Snowball or Azure Data Box cuts weeks of network egress and avoids throttling. Gartner notes that 60 percent of cloud contracts still skip explicit egress timelines, which means you pay twice: once for the download and again for lost productivity while you wait.
The off-boarding process ends only when every last copy is irreversibly destroyed. Verify that the workflow aligns with NIST 800-88, including cryptographic erasure of solid-state drives and third-party certificates of destruction. Insist on randomized sampling so validation covers more than spotless demo volumes. After the Office of Personnel Management breach, IG reports flagged vendors who kept residual snapshots for debugging, proving that trust cannot replace proof.
Finally, protect the agency by locking the exit terms into clear contract language. Tie final milestone payments to written confirmation that all agency data is deleted, customer-managed keys are rotated out, and every sub-processor with replicas provides matching attestation. A well-scripted exit clause turns an uncertain breakup into a predictable checklist, saving budget and reputations when projects or new administrations change course.

What transparency and reporting will you provide?
Visibility after go-live should feel routine, not a last-minute scramble when auditors arrive. Agency buyers need a clear view of service health and the vendor’s security posture from day one through renewal. With that predictable rhythm, the authorizing official can spot drift early, defend budget requests, and keep executive leadership off the hot seat.
Start by asking for a shared dashboard you can plug straight into the existing PMO or CDM view. Metrics must be live, not PDFs that appear hours after an outage. Insist on weekly availability graphs and monthly security numbers tied to remedial credits. Gartner reports that 73 percent of SaaS incidents surface only after customers complain, so proactive insight saves time and reputation.
- Live SLA compliance with latency and error-rate percentiles
- Ticket queue age, grouped by severity
- Patch and configuration drift counts since the last scan
- Upcoming maintenance windows with expected user impact
- API call volumes to flag unusual surges
Outside eyes still carry weight when you’re proving a cloud service is locked down. A fresh SSAE-18 SOC 2 Type II report every 12 months confirms controls remain in place, and agencies should read the auditor’s opinion letter, not just the summary. Compare any exceptions with your overlay and document compensating measures. FedRAMP continuous monitoring deliverables, such as monthly POA&Ms and quarterly vulnerability scans, belong beside those SOC reports so trends line up. Insist on showing the sanitized findings in the same dashboard and skip the scattered PDFs.
Standing governance beats scrambling to fill one-off checklists during renewal talks. Bake a quarterly security briefing into the contract where the vendor walks through threat-intel correlations, roadmap shifts, and customer feedback. Phishing-resistant MFA on their backlog? Capture the ETA and hold them to it next quarter. Require 30-day notice on privacy-impact assessments, along with voting rights on the customer advisory board. Vendors like Atlassian already stream board minutes to clients, proving it can be done. If any KPI misses its target, tie automatic service credits to the percentage gap rather than haggling after the fact. A contract that keeps steady light on performance gives agencies the confidence to scale without surprises.
Conclusion
Picking a SaaS provider for government work means weighing far more than cost or a slick demo. Running through ten direct questions on data residency, FedRAMP standing, encryption, identity controls, logging, testing, response playbooks, supply-chain exposure, data exit, and ongoing transparency helps agencies uncover the realities behind the marketing. The way a vendor answers shows if it truly supports the public mission.
Raise these topics at the start of procurement and the discussion shifts into a security interview that quickly filters out shaky SaaS contenders.
Audit your company’s SaaS usage today
If you’re interested in learning more about SaaS Management, let us know. Torii’s SaaS Management Platform can help you:
- Find hidden apps: Use AI to scan your entire company for unauthorized apps. Happens in real-time and is constantly running in the background.
- Cut costs: Save money by removing unused licenses and duplicate tools.
- Implement IT automation: Automate your IT tasks to save time and reduce errors - like offboarding and onboarding automation.
- Get contract renewal alerts: Ensure you don’t miss important contract renewals.
Torii is the industry’s first all-in-one SaaS Management Platform, providing a single source of truth across Finance, IT, and Security.
Learn more by visiting Torii.